Securely Connect Remote IoT P2P Raspberry Pi Download Mac: The Ultimate Guide
Apr 06 2025
Hey there, tech enthusiasts! Let’s dive straight into the world of IoT (Internet of Things) and P2P (Peer-to-Peer) connections, shall we? If you’re trying to securely connect remote IoT P2P Raspberry Pi download Mac, you’ve landed in the right place. This guide will take you through everything you need to know, from setting up your Raspberry Pi for remote access to ensuring your connection is as secure as Fort Knox. Whether you're a beginner or a seasoned pro, this article has got your back.
In today’s interconnected world, securing your IoT devices is not just an option—it’s a necessity. Imagine leaving your front door unlocked while you’re away. That’s what it feels like when your devices are exposed to potential threats. In this guide, we’ll break down the steps to set up a secure P2P connection using your Raspberry Pi, tailored specifically for Mac users. So, buckle up, because we’re about to embark on a tech-savvy journey!
Before we jump into the nitty-gritty, let’s quickly highlight why this topic matters. According to a recent report by Cybersecurity Ventures, cybercrime is projected to cost the world over $10.5 trillion annually by 2025. Yikes, right? That’s why understanding how to securely connect your IoT devices is more important than ever. Now, let’s get started!
Understanding IoT and P2P Connections
First things first, let’s break down what IoT and P2P mean. IoT refers to the network of physical objects embedded with sensors, software, and connectivity, allowing them to exchange data with other devices and systems over the internet. Meanwhile, P2P is a decentralized communication model where two devices communicate directly without relying on a central server.
Now, here’s the kicker: combining these two technologies can revolutionize how we interact with smart devices. For instance, imagine controlling your home security system remotely or monitoring your smart garden from the comfort of your couch. But wait, there’s a catch—these connections need to be secure, or you risk exposing sensitive data.
Why Secure IoT Connections Matter
Here’s the deal: IoT devices are often seen as low-hanging fruit for hackers. Why? Because many users neglect to secure them properly. A study by Palo Alto Networks found that over 98% of IoT device traffic is unencrypted. That’s like leaving your house keys under the doormat!
- Data Privacy: IoT devices collect a ton of personal data, from your daily routines to your location. If not secured, this data can be misused.
- Device Hijacking: Hackers can take control of your devices, potentially causing chaos in your smart home.
- Network Vulnerability: A compromised IoT device can serve as a gateway for attackers to infiltrate your entire network.
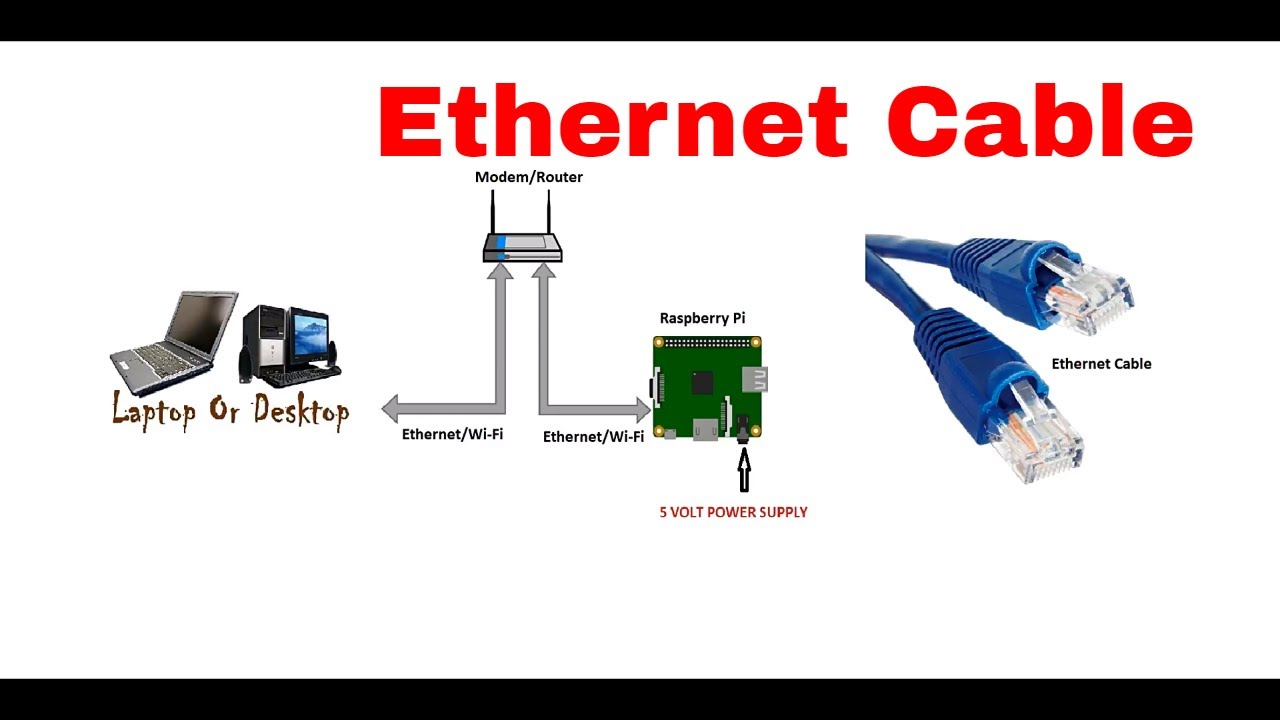
Setting Up Your Raspberry Pi for Remote Access
Alright, now that we’ve covered the basics, let’s get our hands dirty with the Raspberry Pi. This tiny yet powerful device is perfect for IoT projects. To securely connect your Raspberry Pi remotely, follow these steps:
Step 1: Install Raspbian OS
First, you’ll need to install the Raspbian operating system on your Raspberry Pi. Head over to the official Raspberry Pi website and download the latest version. Use a tool like Etcher to flash the image onto an SD card. Once done, insert the card into your Pi and power it up.
Step 2: Enable SSH
SSH (Secure Shell) is your go-to method for remote access. To enable it, create a blank file named "ssh" (no extension) in the boot directory of your SD card. This will activate SSH when your Pi boots up.
Step 3: Set Up a Static IP Address
Having a static IP address ensures that your Raspberry Pi’s address doesn’t change, making it easier to connect remotely. Open the terminal and edit the DHCP configuration file:
sudo nano /etc/dhcpcd.conf
Add the following lines, replacing the IP address with your desired static address:
interface eth0
static ip_address=192.168.1.100/24
static routers=192.168.1.1
static domain_name_servers=192.168.1.1
Securing Your P2P Connection
Now that your Raspberry Pi is set up, it’s time to secure your P2P connection. Here’s how you can do it:
Use Encryption Protocols
Encryption is your best friend when it comes to securing data. Implement protocols like TLS (Transport Layer Security) or SSH to encrypt your P2P communications. This ensures that even if someone intercepts your data, they won’t be able to decipher it.
Implement Firewall Rules
A firewall acts as a digital bouncer, controlling who gets in and out of your network. Use tools like ufw (Uncomplicated Firewall) to set up rules that restrict access to your Raspberry Pi. For example:
sudo ufw allow ssh
This command allows SSH traffic while blocking everything else.
Regularly Update Your Software
Keeping your software up to date is crucial. Regular updates patch vulnerabilities and protect your devices from emerging threats. Set up automatic updates to ensure your Raspberry Pi is always running the latest version of Raspbian.
Downloading and Configuring on Mac
If you’re a Mac user, fear not! Setting up your Raspberry Pi for remote access is just as easy on macOS. Here’s how you can do it:
Install VirtualBox or VMware
While not strictly necessary, using a virtual machine can simplify the process. Download VirtualBox or VMware and install the Raspbian OS on a virtual machine. This allows you to test and configure your setup without needing a physical Raspberry Pi.
Use SSH Clients
Mac comes with a built-in SSH client, so you don’t need to install anything extra. Open Terminal and type:
ssh pi@192.168.1.100
Replace the IP address with your Raspberry Pi’s address. Enter the password when prompted, and you’re in!
Best Practices for Secure Connections
Here are some additional tips to keep your IoT P2P connections secure:
- Use Strong Passwords: Avoid using common passwords like "password123." Instead, opt for complex combinations of letters, numbers, and symbols.
- Change Default Settings: Always change default usernames and passwords on your devices.
- Monitor Activity: Regularly check your device logs for any suspicious activity.
Common Challenges and Solutions
Let’s face it, setting up secure IoT connections isn’t always a walk in the park. Here are some common challenges and how to overcome them:
Challenge 1: Connectivity Issues
If you’re struggling to connect to your Raspberry Pi remotely, double-check your network settings. Ensure that your router allows port forwarding and that your Pi’s IP address is correctly configured.
Challenge 2: Security Breaches
In case of a security breach, act fast! Disconnect the affected device from the network, perform a thorough scan for malware, and reset all passwords.
Future Trends in IoT Security
The world of IoT is evolving rapidly, and so are the security measures. Here are some trends to watch out for:
- AI-Powered Security: Artificial intelligence is being used to detect and respond to threats in real time.
- Blockchain Technology: Blockchain offers a decentralized and tamper-proof way to secure IoT communications.
- Quantum Encryption: While still in its infancy, quantum encryption promises unbreakable security for IoT devices.
Conclusion
And there you have it, folks! A comprehensive guide on how to securely connect remote IoT P2P Raspberry Pi download Mac. By following the steps outlined above, you can ensure your devices are protected from potential threats. Remember, security is an ongoing process, so stay vigilant and keep learning.
Before you go, why not drop a comment below and let us know what you think? Did we miss anything? Are there any other topics you’d like us to cover? Don’t forget to share this article with your tech-savvy friends. Together, let’s make the IoT world a safer place!
Table of Contents
- Securely Connect Remote IoT P2P Raspberry Pi Download Mac: The Ultimate Guide
- Understanding IoT and P2P Connections
- Why Secure IoT Connections Matter
- Setting Up Your Raspberry Pi for Remote Access
- Step 1: Install Raspbian OS
- Step 2: Enable SSH
- Securing Your P2P Connection
- Use Encryption Protocols
- Downloading and Configuring on Mac
- Install VirtualBox or VMware
- Best Practices for Secure Connections
- Common Challenges and Solutions
- Future Trends in IoT Security
- Conclusion